HTTP(S)
Hyper Text Transfer Protocol (Secure)
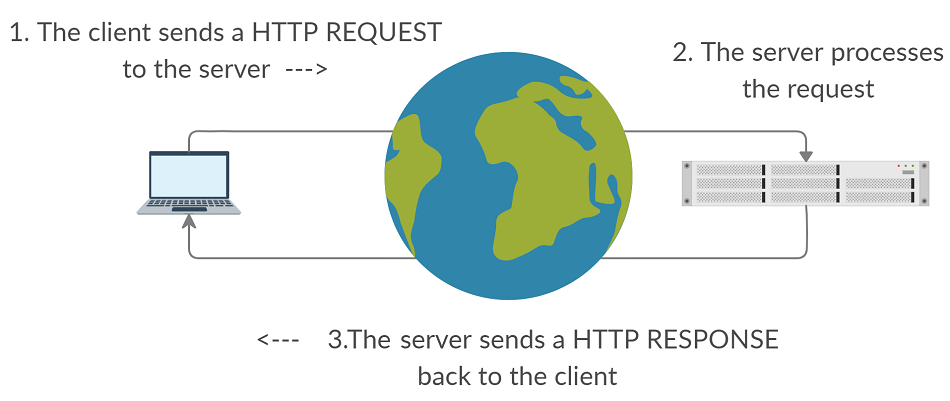
HTTP is the foundation for how website data (HTML Files, Images) is sent and received on the internet.
HTML is a stateless and connectionless protocol that operates at the Application Layer of the IP protocol stack. A request is made by a client computer (usually by a web browser) and the server then sends a response to the client.
Types of HTTP Requests
Common types of HTTP requests include:
- GET – This is a request for data from a web server(such as a HTML page or a CSS file)
- POST – This is where data is sent to a web server (such as the contents of a form that the user has filled in)
- PUT – This requests that a file on a server be updated
- DELETE – The requests that a file on a server be deleted.
- More request types can be found here.
Response Codes
When a page or file is requested the server usually sends a response code with the response.
Common HTTP Response Codes Include:
- 200 – OK
- 300 Moved Permanently. The URL of the requested page has been moved permanently
- 401 Unauthorized. The client has not been authenticated with the system.
- 403 Forbidden. The client is authenticated but does not have the access privileges to perform the action.
- 404 Not Found. The requested resource cannot be found at the location specified.
- 500 Server Error. The server have encountered an internal error somewhere.
FTP(S)
File Transfer Protocol (Secure)
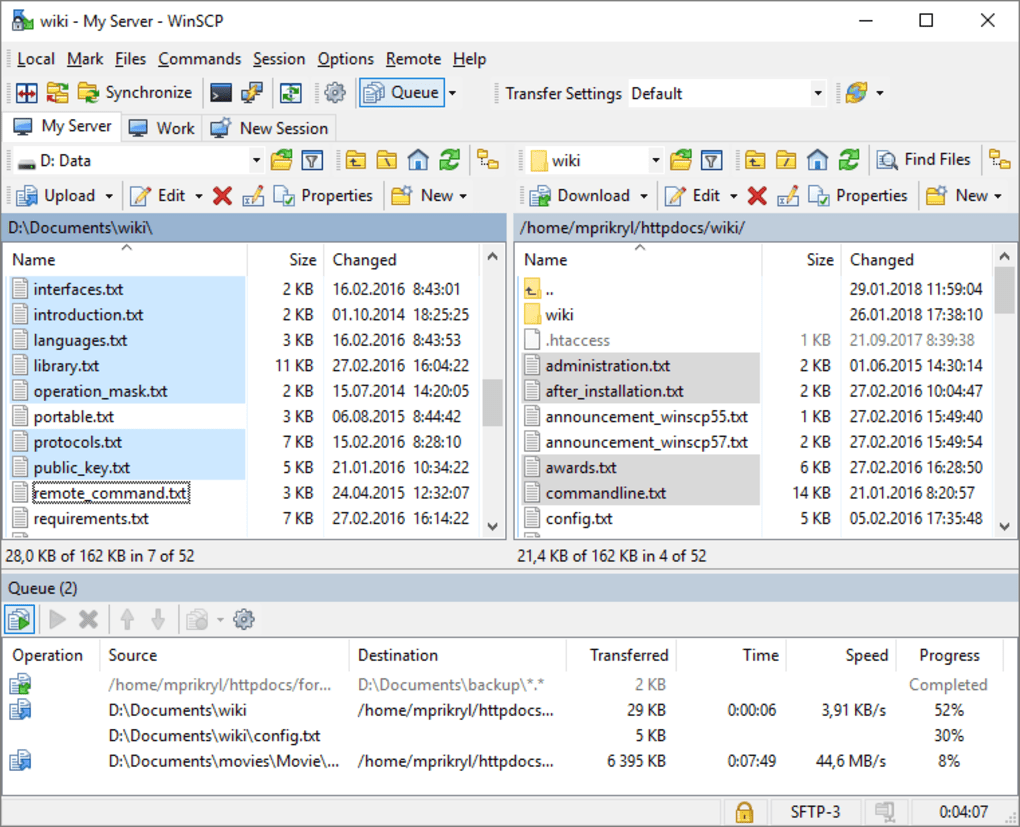
Original protocol used to transmit and receive files over the internet. FTP is a stateful connection, meaning a connection between client and server is established and maintained for the duration of use.
Can be used by:
- Web Browsers to download files
- FTP Programs to upload to/download from servers on the internet. Example software includes WinSCP, FileZilla.
SMTP
Simple Mail Transfer Protocol
SMTP is used for sending out email from an email client (such as Outlook / Apple Mail) to an email server. It is also used for relaying email messages from one server to another, which is necessary if the sender and recipient use different email server providers.
POP3
Post Office Protocol
POP3 is used to retrieve email messages from a server for display within an email client on the client pc. POP3 is different from POP because it contains additional authentication systems that stop unauthorized/malicious email access.
The POP procedure is as follows:
- Connect to the email server and authenticate
- Retrieve outstanding emails from the server
- Delete retrieved emails from the server (optional)
- Disconnect from the server
IMAP
Internet Message Access Protocol
This protocol is similar to POP3 except that it offers more functionality, such as:
- Mail Synchronization
- Multiple Folder based organization on the web server.
IMAP is the most common protocol to be used by large organizations for mail retrieval.
BitTorrent
BitTorrent
BitTorrent is a Peer-to-Peer file sharing protocol used for high speed transfer of large files across the internet. It differs from downloading from a normal server in that you don’t download the file from a single file server, but from multiple peers.
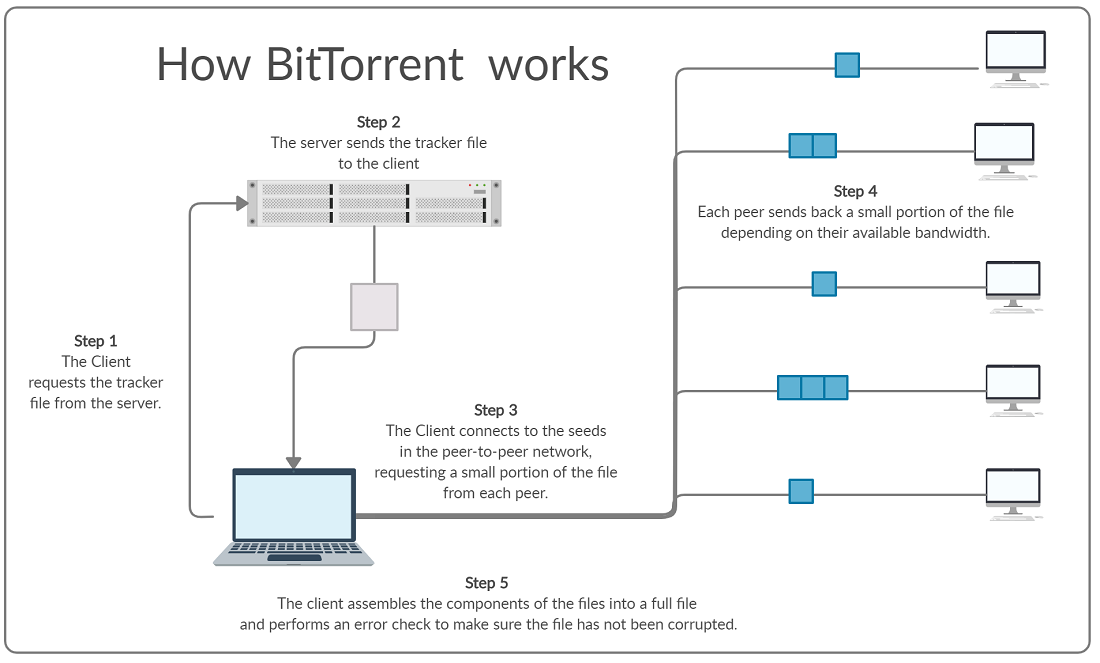
How it works
A Central Server contains the tracker file. This file does not contain the file you wish to download, but it contains the IP addresses of current seeds for the file, as well as other information about the file that is used to reassemble the file and check for errors.
A seed is a peer on the network who is hosting the file for download and hosting a file for download is known as seeding. When you download a file via BitTorrent the Client software your computer connects to multiple different seeds and downloads a small portion from each. Because you are downloading from multiple sources at once your client is able to achieve higher download speeds than if multiple clients were all connected to one server. Downloading a file is known as leeching. The total collection of seeding & leeching clients on the network are known as the swarm.
Once the complete file has been downloaded it needs to be checked to ensure that it has been fully downloaded correctly. This is achieve through the use of a checksum.
Resources
Resources