Client - Server Networks
Client – Server Networks
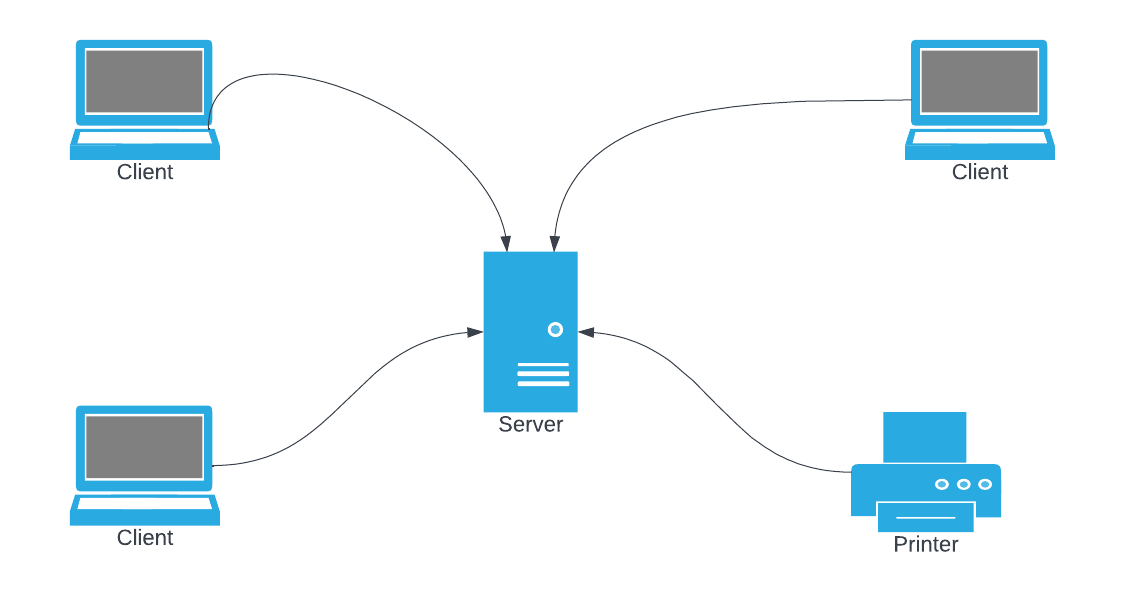
A logical view of a client-server network. Note that extra physical hardware is not shown on the logical view.
Most organisations use a form of client – server networks. This is where access to network resources and overall control of the network is governed by the server. A server is a special kind of computer that is designed to cope with a large number of requests at the same time.
Servers control:
- User access levels and authentication
- File access and backup
- Hardware resource sharing(such as printers and scanners)
- Internet connection sharing and access control
Users log on to client computers, which connect to the network and access the shared resources.
Advantages
- Centralized Management: Client-server networks provide centralized management of resources, data, and security. The server acts as a central point of control, making it easier to manage and secure data and resources in a consistent manner.
- Scalability: Client-server networks are scalable, allowing additional clients to connect to the server without affecting the overall network performance. This makes it easier to accommodate a growing number of users or devices.
- Resource Sharing: Centralized servers enable efficient resource sharing. Resources such as printers, storage devices, or databases can be shared among multiple clients, reducing costs and improving efficiency.
- Enhanced Security: Client-server networks offer improved security compared to peer-to-peer networks. Access controls and security measures can be implemented at the server level, protecting sensitive data and preventing unauthorized access.
- Robustness and Reliability: With a dedicated server handling requests and managing resources, client-server networks tend to be more reliable. Servers can be equipped with redundant components and backup systems to ensure high availability.
Disadvantages
- Cost: Implementing and maintaining client-server networks can be more expensive compared to peer-to-peer networks. Servers, network infrastructure, and skilled IT personnel are required, which can increase the overall cost.
- Single Point of Failure: Client-server networks rely on a central server. If the server fails or experiences downtime, it can disrupt network operations and impact the accessibility of shared resources.
- Network Complexity: Client-server networks can be more complex to set up and configure compared to peer-to-peer networks. Proper planning, network design, and administration are necessary for efficient operation.
- Dependency on Network Performance: The performance of client-server networks heavily relies on network bandwidth and latency. If the network experiences congestion or latency issues, it can affect the responsiveness and performance of client-server applications.
- Potential Bottlenecks: The server may become a bottleneck if it becomes overloaded with requests or if it lacks sufficient resources to handle the client’s demands. This can result in decreased performance for clients.
Peer to Peer Networks
Peer to Peer Networks

Peer to Peer networks are that are usually temporary and quick to set up. They are usually used for temporary file and resource sharing, where a larger client-server network is not needed. Each device connected to a Peer to Peer network is a node, and each node forwards on data to all other nodes in range.
Advantages
- Quick, easy and cheap to set up – no server, switch or routers required.
- Decentralised, meaning that if one ‘node’ goes down, the network still remains up.
- Some peer-to-peer networks (such as TOR networks) allow users to communicate anonymously, making it difficult to trace user activity.
Disadvantages
- No access the the facilities that servers provide ( file backup, use authentication)
- Less secure than standard networks