Accident
Accidental Damage
One of the most common issues with network security is the risk of accidental damage to the network hardware and software due to accidents on the part of the user.
These threats include:
- Accidentally deleting/altering files on the network. This is probably the most common issue and is also one of the most easily solved
- Accidental damage to network hardware by tripping over cables or pouring liquids onto hardware such as computers, switches or routers.
- Accidentally distributing sensitive data to unauthorized people.
Phishing
Phishing
Phishing is a very common form of attack, using using emails. Attackers send emails purporting to be from organisations such as banks and ecommerce sites, with the aim of tricking users in to clicking on the email links and divulging personal information, especially:
- Usernames
- Passwords
- Credit / Debit card information
Spotting Phishing Emails
Phishing emails are often(but not always) easy to spot. Common giveaways include:
- The email does not contain your real name, just ‘Dear Sir’ or your email address.
- There are multiple spelling and grammar mistakes in the email
- The email originates from a misspelt version of the email domain . e.g. hotmall.com instead of hotmail.com.
- The email tries to scare to into immediate action
- The email requests your banking details or your account password / pin.
Pharming
Pharming
This attack centres around poisoning the DNS cache on either a computer, server or router, with the intention of redirecting a user’s browser to a fake version of a website when the user types in a domain name.
When you type in a web address (e.g. www.amazon.co.uk) the browser needs to lookup the IP address (e.g. 96.127.32.0) that matches the domain name. It is to this address that the request to load the page is send. If a hacker is able to alter the contents of the DNS cache then your browser will be passed the wrong IP address and you will be redirected to the fake site without noticing.
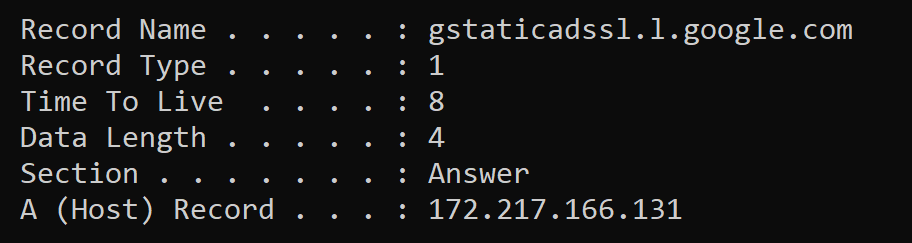
Want to see your computer’s DNS cache? Open a CMD prompt and type in ipconfig /displaydns
Threat Reduction Measures
- Most websites now use SSL certificates. These certificates are used by your browser to ensure that the site is genuine.
- Most browsers and anti-virus products keep an up to date list of servers that host fake content and warn the users before a page is known.
People
Social Engineering ( People)
Social engineering covers a wide range of attacks where people are tricked in to divulging personal information or harming /compromising a system.
Brute Force
Brute Force Attacks

This is useful again systems where either the website / system allows unlimited login attempts. The attacker keeps trying every possible password combination until they are successful. This form of attack is usually combined with a dictionary attack and is especially effective where short or common passwords are used (e.g. password123)
Activity
See how long it would take for your favourite password to be hacked using the following site:
https://random-ize.com/how-long-to-hack-pass/
https://howsecureismypassword.net/
DOS
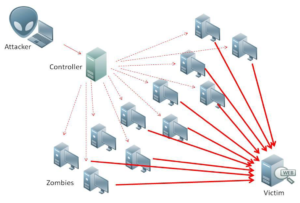
DOS/ DDOS – denial of service attacks / Distributed Denial Of Service Attacks
Often an objective of attackers is to shut down a webserver or website. A simple way of achieving this is to overload the site with thousands and thousands of requests for data. The server is overloaded with requests and it crashes. This is known as a Denial Of Service Attack.(DOS)
In order to defend attack such an attack, webservers often block requests from an IP address if it starts to send too many requests. The only way to circumvent this defence is to attack the server from many machines, in many locations at once. This can only be achieved if you first find a vulnerability in client computers (or more recently Internet Connected Devices like webcams, Network Attached Storage, Smart devices). You take control of these devices and turn them in to a large BOTNET, getting thousands or millions of hacked devices to send requests to the intended target. This type of attack of known as a Distributed Denial of Service Attack.
Interception
Data interception and Theft
With the widespread adoption of WIFI in offices around the world, data interception has become widespread. Encrypted packets can be sniffed, and given enough packets and time, the WIFI encryption key can be computed and access to the network can be obtained. This is especially effective against older, weaker encryption technologies, for example WEP (Wired Equivalent Privacy)
SQL Injection
SQL Injection
An SQL Injection works by taking advantage of poor programming discipline while programming using SQL databases.
If user inputs are not sanitized (checked to make sure no illegal input has been entered) before processing, then an attacker can inject their own SQL statements in to the system.
Weak Python/SQL Code Example
- fname = input(“What’s you first name?”)
- lname = input(“What’s your last name?”)
- c.execute(“INSERT INTO STUDENTS VALUES(‘”+ fname + “‘,'”+lname+”‘);”)
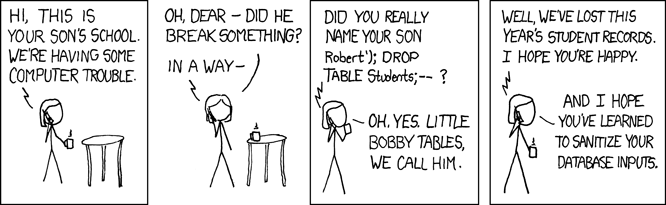
In the example above the user input on lines 1 and 2 are directed added to the SQL statement using string concatenation, this allows the attack shown in the cartoon above to take place.
Strong Python/SQL Code Example
- fname = input(“What’s you first name?”)
- lname = input(“What’s your last name?”)
- entry = (fname,lname)
- c.execute(“INSERT INTO STUDENTS VALUES(?,?);”,entry)
In the example above the user input is first added to a tuple and then passed to execute function as an function parameter. This input is then sanitized internally within the execute function before being passed to the SQL query for processing.
Network Policy
Poor Network Policy
When network administrators set up the network policy, they may implement poor policies which allow a vector of attack by attack by hackers.
Examples include:
- Allowing weak passwords
- Not compartmentalizing data access
Resources