Intro
Virtual Private Networks
A Virtual Private Network (VPN) is a technology that allows you to create a secure and encrypted connection over a less secure network, such as the internet. VPNs are commonly used for various purposes, including enhancing online privacy and security, accessing region-restricted content, and establishing secure connections for remote work or business purposes.
How VPNs Work
1. Data Encryption Before It Leaves Your Device
When you connect to a VPN, the software (a VPN client) running on your device immediately encrypts your internet traffic. This means that your emails, web browsing, app data, or anything else being sent is converted into unreadable code using complex encryption algorithms.
2. Secure Tunnel to the VPN Server
The encrypted data is then encapsulated in a secure tunnel, which is a private connection between your device and the VPN server.
This tunnel is set up using VPN protocols (like OpenVPN, WireGuard, or IPsec) and ensures that your data travels safely across the internet, hidden from outsiders.
3. Data is Decrypted at the VPN Server and Sent to the Destination
Once your encrypted data reaches the VPN server, it gets decrypted (unlocked) and sent to the final destination — this could be a:
-
Website (like google.com),
-
App server (like for Netflix or Gmail),
-
Or a private network (like your company’s internal systems).
Because the data appears to be coming from the VPN server (not your actual device), this also hides your IP address, adding another layer of privacy.
4. Response Data Travels Back Through the Same Tunnel
When the destination (e.g. the website) sends data back — like a web page or a video — that data first goes to the VPN server, which encrypts it again and sends it back through the secure tunnel to your device.
Your VPN client then decrypts the data, making it readable again.
Remote Access
Remote Access VPN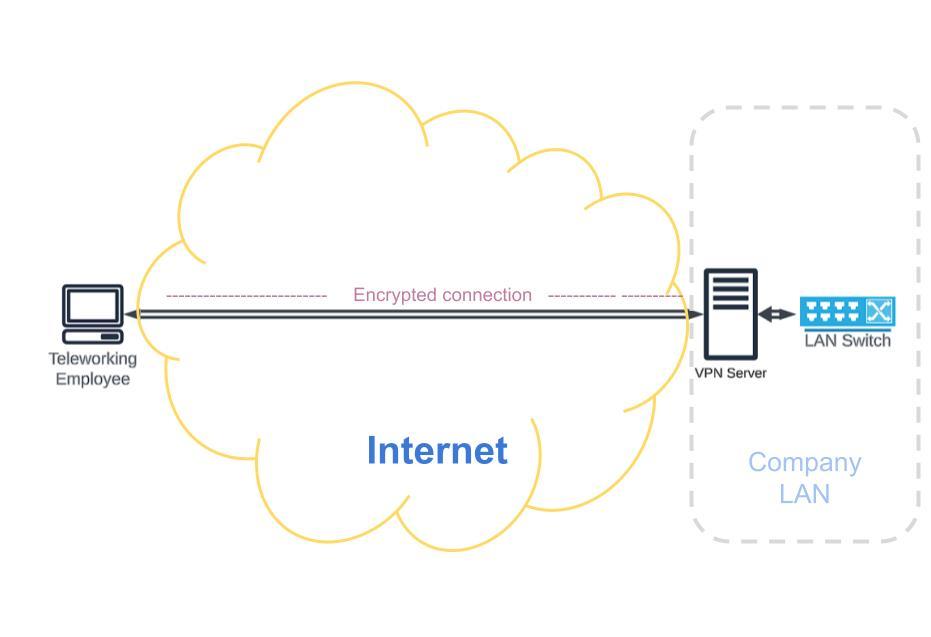
Businesses often use VPNs to provide remote employees with secure access to the company’s internal network and resources. This allows employees to work from home or other remote locations while maintaining a secure connection to company servers and data.
-
Connects individual users to a private network (e.g., company employees working from home).
-
Requires VPN client software.
-
Tunnels are created from the user’s device to the company’s network.
🔧 Use case: A remote employee securely accessing internal company files.
Public Networks
Public Wi-Fi Security VPN
When using public Wi-Fi networks, which can be less secure, a VPN can provide an extra layer of security by encrypting your internet traffic and protecting your data from potential threats on the network.
Site to Site
Site to Site VPN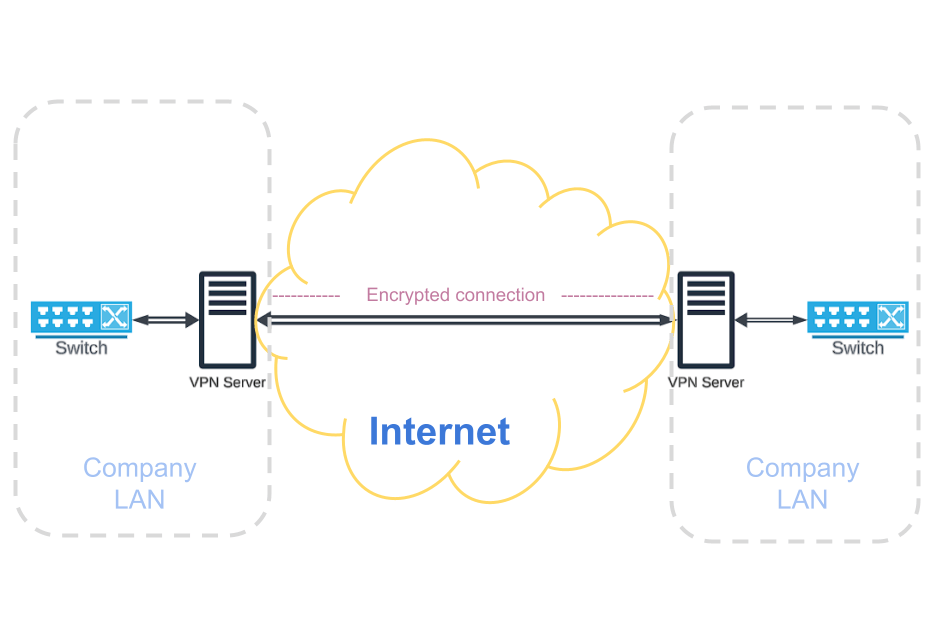
These are used to connect multiple offices or branches of a company’s network securely, creating a virtual network over the internet.
-
Connects two entire networks, usually company branches in different locations.
-
Devices on one site can access resources on the other site as if they were on the same local network.
How it works
-
Each site has a VPN gateway (usually a router or firewall).
-
These gateways authenticate each other and establish a VPN tunnel between them.
-
Once the tunnel is established, data travels securely between sites.
- Use case: A company HQ in London and a branch office in Manchester sharing a single internal system securely over the internet.
IP Spoofing
IP spoofing VPN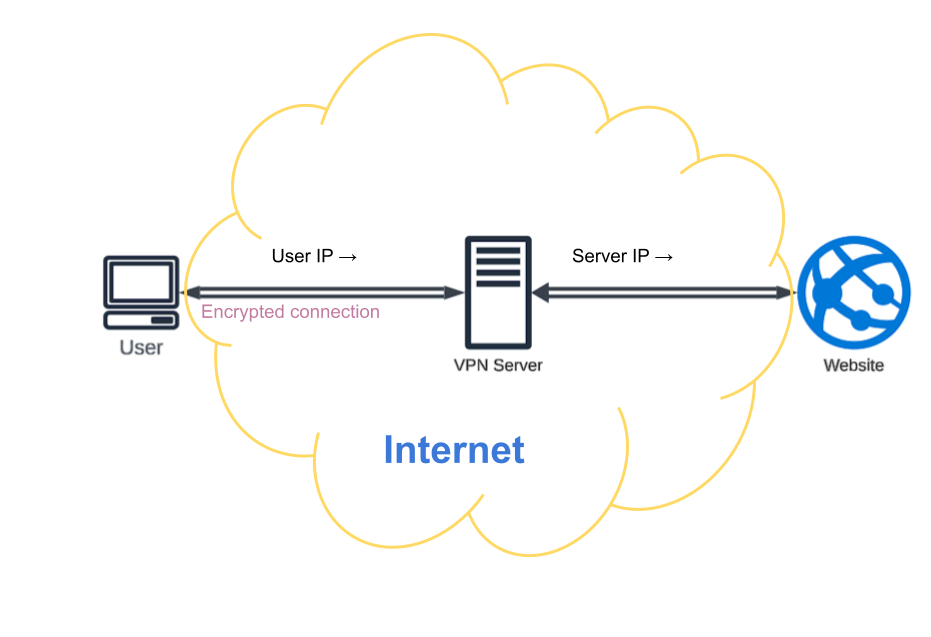
VPNs can mask your real IP address using a proxy server, making it harder for websites and online services to track your location and online behavior. This can enhance your anonymity and privacy online, as well as allow access to geo-restricted content.
IPSec
VPN Protocols
IPSec (Internet Protocol Security)
-
Used for: Site-to-site VPNs and some remote-access VPNs.
-
How it works: IPSec operates at the network layer (Layer 3) of the OSI model, meaning it can encrypt and authenticate all traffic between two IP addresses—regardless of the applications generating that traffic.
-
Two key modes:
-
Transport Mode – Only the data portion of a packet is encrypted.
-
Tunnel Mode – The entire packet is encrypted and then encapsulated in a new packet. This is most common for site-to-site VPNs.
-
Why it’s useful: IPSec is widely used in enterprise settings where two offices or sites need to be connected securely over the internet. It’s robust, widely supported, and often paired with other protocols like IKEv2.
OpenVPN
OpenVPN
-
Used for: Both remote-access and site-to-site VPNs.
-
How it works: OpenVPN is an open-source protocol that uses SSL/TLS for encryption. It runs in user space, which means it doesn’t need to be built into the operating system.
-
Highly configurable – You can choose from various ports (UDP or TCP), encryption methods, and authentication mechanisms.
Security: Very secure when configured correctly — it supports AES encryption, certificates, and even two-factor authentication.
Performance: Generally fast and reliable, although slightly slower than WireGuard due to more complex encryption processes.
Bonus: OpenVPN is open-source, which means it’s constantly being improved and audited by the community.
IKEv2
IKEv2 (Internet Key Exchange version 2)
-
Used for: Remote-access VPNs, especially on mobile devices.
-
How it works: IKEv2 is often used in combination with IPSec to create a fast and secure VPN tunnel. It’s designed to handle network switching — so if your connection drops or you switch from Wi-Fi to mobile data, the VPN connection automatically re-establishes itself.
Benefits:
-
Very fast connection setup.
-
Strong support for modern encryption algorithms.
-
Especially useful for mobile users who move between networks (e.g., from home Wi-Fi to 4G).
📱 Platform support: Built into iOS, Android, Windows, and macOS.
SSL
SSL/TLS (Secure Sockets Layer / Transport Layer Security)
-
Used for: Remote-access VPNs, especially those accessed via a web browser (also known as SSL VPNs).
-
How it works: SSL/TLS is the same encryption technology that secures HTTPS websites. With SSL VPNs, the user connects to a VPN gateway through a web browser, which creates a secure, encrypted session.
Pros
Advantages
Enhanced Privacy and Security
VPNs encrypt your internet traffic, making it extremely difficult for third parties, such as hackers, ISPs, and government agencies, to monitor your online activities. This encryption helps protect your personal data, including passwords, credit card information, and browsing history, from potential threats.
Anonymous Browsing
By masking your IP address, VPNs enable you to browse the internet more anonymously. Websites and online services won’t be able to track your location, and your online behavior becomes more private.
Access to Geo-Restricted Content
VPNs allow you to bypass geographical restrictions and access content and services that might be blocked or limited in your region. By connecting to servers in different countries, you can appear as though you are located in that country, giving you access to region-specific content.
Security on Public Wi-Fi
When using public Wi-Fi networks in places like cafes, airports, or hotels, your data can be vulnerable to cyberattacks. VPNs add an extra layer of security by encrypting your internet traffic, protecting your data from potential threats on the network.
Circumvent Censorship and Surveillance
In countries with strict internet censorship or surveillance, VPNs can provide a means to access blocked websites and communicate more freely. They can help users evade government-imposed restrictions on online content and communication.
Cons
Disadvantages
Reduced Internet Speed
VPNs can slightly slow down your internet connection due to the encryption and routing processes. The extent of the slowdown depends on various factors, including the VPN service provider and the distance to the VPN server.
Cost
Most reputable VPN services require a subscription fee. While there are free VPN options available, they often come with limitations and may compromise your privacy and security.
Complexity
Setting up and configuring a VPN can be challenging for some users, especially those who are not tech-savvy. Additionally, troubleshooting VPN issues can be more complex than typical internet connectivity problems.
Limited Accessibility
Some websites and online services may block or restrict access to users connected via VPNs, as they try to combat fraudulent activities. This can be frustrating when trying to access specific content or services.
Legal and Policy Issues
The use of VPNs may be subject to legal restrictions in some countries. Users should be aware of the laws regarding VPN usage in their jurisdiction and any potential consequences.
Trust in VPN Providers
VPNs rely on the service provider’s infrastructure. Users must trust the provider not to log or misuse their data. It’s crucial to choose a reputable VPN service with a strong commitment to privacy and security.
No Absolute Anonymity
While VPNs enhance privacy and security, they do not provide absolute anonymity. Law enforcement agencies and skilled adversaries can potentially trace VPN traffic back to the user, especially if the VPN service keeps logs.