Digital Certificates
Digital Certificates
One of the limitations of asymmetric encryption is that when used on its own, it is vulnerable to a man-in-the-middle attack. It is possible for an attacker to intercept the asymmetric handshake process and fool the sender and receiver into thinking they are sending secure messages. This is because although asymmetric encryption ensures secure transfer of data between two parties it does not itself ensure authentication of the identity of the parties involved. In order to ensure authentication asymmetric encryption needs to be used in conjunction with a digital certificate issued by a trustworthy certificate authority.
When an entity (such as a website) wants to apply for a digital certificate they send their public key, along with other details, to the certificate authority(CA). The CA then sends a signed copy of the digital certificate back to the entity.
Verification
Certificate verification process (for a website)
Step 1 – Certificate Requested
The user’s browser sends a message to the website server, requesting the digital certificate.
Step 2 – Certificate Sent
The website sends a copy of the digital certificate to the user.
Step 3 – Certificate Authenticated
The user’s browser verifies the validity of the certificate using the public key of the CA. Most web browsers have a preinstall cache of the public keys of trusted Certificate Authorities. The public key stored on the browser is used to verify the hash digest of the certificate.
Step 4 – Communication Begins
The user’s browser uses the public key provided within the authenticated certificate to perform asymmetric encryption on the symmetric shared key and sends the encrypted symmetric key to the website. Since only the website know the corresponding private key, only the legitimate website can decrypt the encrypted symmetric key and therefore communication can be considered secure and authenticated.
Contents of a Digital Certificate
- Name of the Owner – A unique identifier for that particular owner
- Public Key of the owner
- Issue Date of the certificate
- Expiry Date
- The Name of the Certificate Authority
- Digital Certificate of the Certificate Authority (This is a hash of the above items, generated using the CA’s private key.
Digital Certificates Video
SSL Certificates Video
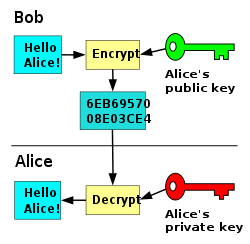
Keys
Public & Private Keys
Public and private keys are core components of asymmetric cryptography, also known as public-key cryptography. The public and private keys are mathematically related in such a way that data encrypted with one key can only be decrypted with the other key.
The public key is intended to be shared openly and is often associated with an individual or entity. Anyone can use the public key to encrypt data or verify digital signatures, but it cannot be used to decrypt data.
The private key is used for decrypting data that has been encrypted with the corresponding public key and for creating digital signatures.. It must be kept secret and should never be shared with anyone.
Key Exchange
Key Exchange
When a website and client establish a connection they each send their public key to the other and all subsequent data is encrypted using the recipients public key before sending. This means that only the intended recipient can decrypt the message.
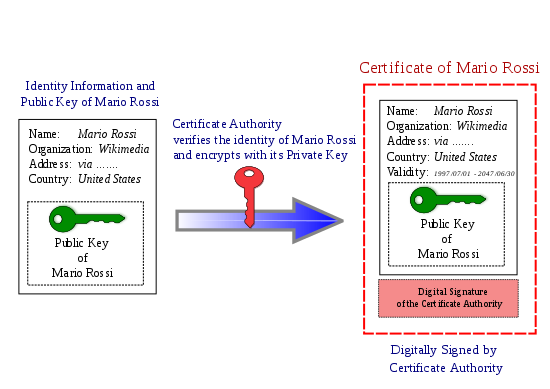
CAs
Certificate Authorities.
Certificate Authorities (CAs) are trusted organisations who are responsible for issuing, managing, and verifying the digital certificates that websites use to prove who they are. They are used to ensure that your browser has connected to the website you think you have connected to and you have been the victim of DNS hijacking.
Websites are issued digital certificates by CAs and the certificate is encrypted using the private key of the CA. When a website communicates with a client it sends this certificate and the browser uses the public key it has been given directly by the CA to decrypt the digital certificate, verifying that the website is legitimate.
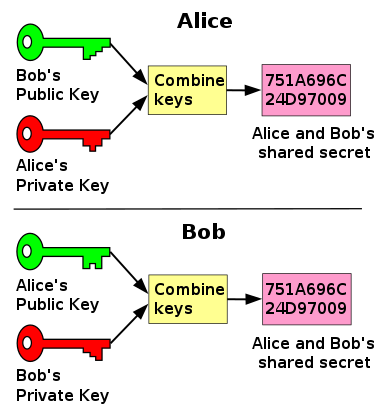
Diffie-Hellman
Diffie-Hellman
One of the disadvantages of asymmetric encryption is that it is computationally expensive, making it too inefficient for high speed data transmission, such as video streaming.
Once a client and server has established a connection they switch more efficient symmetric encryption using the Diffie-Hellman key-exchange technique of combining public-private key pairs in order produce a shared secret which can be used to encrypt data.
Signatures
Digital Signatures