Introduction
Introduction to Asymmetric Encryption
The Problem with symmetric encryption
Symmetric encryption is great for encrypting data when both the sender and receiver are in possession of the shared symmetric key. However this form of encryption requires the key to be shared before use. This is a problem on open networks such as the internet as often you will need to communicate with websites or individuals who you don’t know. You can’t send the shared key across the network unencrypted as an eavesdropper could intercept the communication and retrieve the key.
We need a method of encryption that can provide secure communication between two parties that are unknown to each other. In this instance we need to use Asymmetric Encryption.
Encryption Process
Asymmetric encryption uses public key and private key pairs in order to solve the problem. These two encryption keys are generated together and are mathematically related, with the private key being the key that decrypts any data encrypted with the public key.
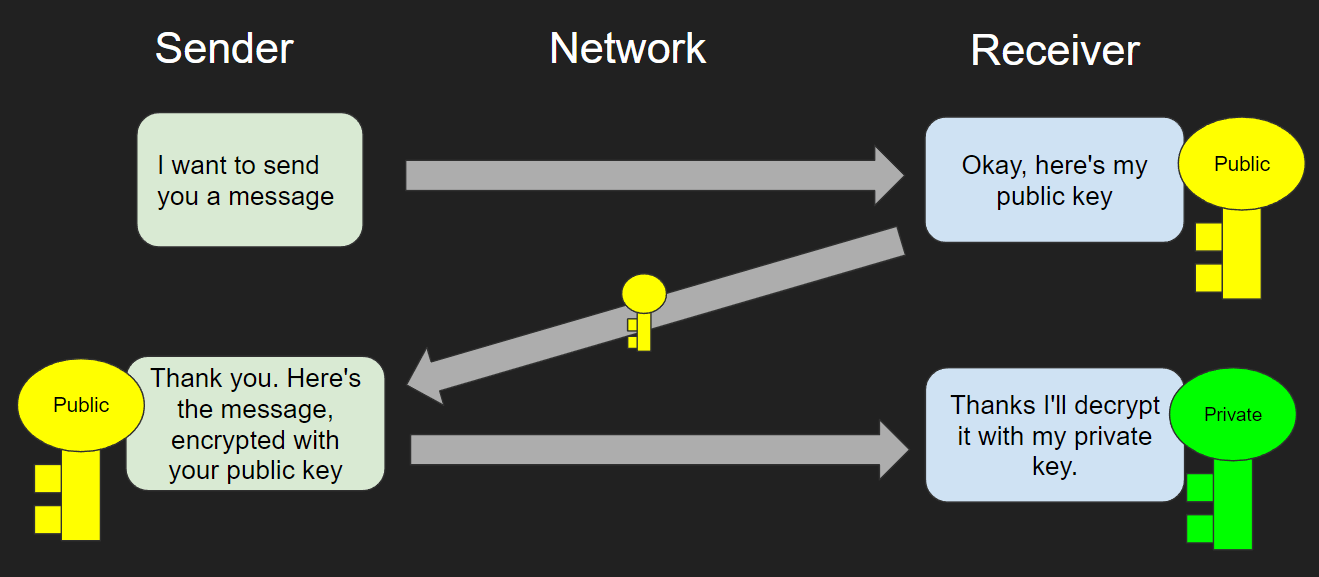
The Asymmetric Encryption Process
The Public Key
This key is shared publicly and is used by the sender to encrypt the data they wish to send to the receiver.
The Private Key
This key is kept secret by the receiver and it is never shared as it is the key that is used to decrypt the encrypted data.
Basic Videos
Asymmetric Message Sending
Advanced Videos
Asymmetric Encryption Videos
Diffie-Hellman Key Exchange
Mathematics
Resources
Resources
In depth guide to symmetric and asymmetric encryption
Past Paper Questions
May June 21 Question 6 Paper 31
Summer 2020 Paper 31 – Question 8
Summer 2019 Paper 31 – Question 5
Summer 2019 Paper 32 – Question 8
Winter 2018 Paper 32 – Question 6
Summer 2018 – Paper 32 – Question 5
Summer 2016 Paper 31 – Qn2C (Email encryption)