Protocols
Network Protocols
Network protocols are sets of rules and procedures that govern the communication and interaction between devices in a computer network. They define how data is transmitted, received, formatted, addressed, and processed across a network.
Network protocols are required to ensure standardized communication, reliable data transmission, addressing and routing, error detection and correction, security, network management, interoperability, and support for specific applications and services within computer networks.
Standard Network Protocols Included in the Edexcel iGCSE Course Include:
- Ethernet (IEEE 802.3)
- Wi-Fi (IEEE 802.11)
- Internet Protocol (IP)
- Transmission Control Protocol (TCP)
- Domain Name System (DNS)
- Simple Mail Transfer Protocol (SMTP)
- File Transfer Protocol (FTP)
- Hypertext Transfer Protocol (HTTP)
- Virtual Private Network (VPN)
- Network File System (NFS)
Other common protocols not required in the Edexcel iGCSE Course include:
- User Datagram Protocol (UDP)
- Internet Control Message Protocol (ICMP)
- Border Gateway Protocol (BGP)
- Dynamic Host Configuration Protocol (DHCP)
- Secure Shell (SSH)
- Secure Sockets Layer (SSL) / Transport Layer Security (TLS)
- Simple Network Management Protocol (SNMP)
- Network Time Protocol (NTP)
Ethernet
Ethernet Protocol
Ethernet is a widely used networking protocol that defines the standards for wired local area networks (LANs). It provides a set of rules and procedures for devices to communicate with each other over a shared physical medium, such as twisted pair copper cables or fiber optic cables.
The Institute of Electrical and Electronics Engineers (IEEE) is responsible for developing and maintaining Ethernet standards. The most widely adopted standard is IEEE 802.3, which defines various Ethernet specifications and variants.
Ethernet has evolved over time, offering higher data rates, improved efficiency, and additional features. It is the foundation of local area networking and is widely used in homes, offices, data centers, and enterprise networks for connecting devices and facilitating communication between them.
Key Features:
- Physical Layer – Ethernet specifies the physical layer characteristics, such as the type of cable, connectors, and signaling used for data transmission. Various versions of Ethernet, such as 10BASE-T, 100BASE-TX, and 1000BASE-T, define different data rates and media types.
- Data Link Layer – Ethernet operates primarily at the data link layer of the OSI model. It uses a frame-based protocol, where data is encapsulated into Ethernet frames. The data link layer is responsible for addressing, error detection, and flow control.
- Ethernet Frames – An Ethernet frame consists of various fields, including source and destination MAC addresses, type or length field, data payload, and a cyclic redundancy check (CRC) for error detection.
- MAC Addresses – Ethernet devices are identified by unique MAC addresses, which are assigned by the manufacturer. MAC addresses are typically represented as six pairs of hexadecimal digits (e.g., 00:1A:2B:3C:4D:5E) and are used for communication and addressing within an Ethernet network.
- Switching – Ethernet networks often use switches to forward data between devices. Switches examine the destination MAC address in the Ethernet frames and forward them to the appropriate port, enhancing network efficiency and reducing collisions.
Wifi Protocol
Wifi Protocol
Wi-Fi (Wireless Fidelity) is a wireless communication technology that allows devices to connect to a local area network (LAN) or the internet without the need for physical wired connections. It is based on the IEEE 802.11 standard, which defines the specifications for wireless local area networks (WLANs). Wi-Fi enables wireless networking and internet access for a wide range of devices, including smartphones, laptops, tablets, smart home devices, and more.
Wi-Fi has become ubiquitous in homes, offices, public spaces, and other environments, providing wireless connectivity and internet access for a wide range of devices. It offers convenience, flexibility, and mobility, allowing users to connect and communicate wirelessly within a local network or access the internet without the need for wired connections.
Key Features
- Frequency Bands – Wi-Fi operates in the 2.4 GHz and 5 GHz frequency bands, which are unlicensed and globally available for use. These frequency bands are divided into multiple channels, and Wi-Fi devices use various modulation and encoding techniques to transmit and receive data over these channels.
- Standards – The IEEE 802.11 standard family encompasses different versions and variations of Wi-Fi protocols. Some common Wi-Fi standards include 802.11b, 802.11g, 802.11n, 802.11ac, and 802.11ax (also known as Wi-Fi 6).
- SSID and Authentication – Wi-Fi networks are identified by a Service Set Identifier (SSID), which is a unique name assigned to each wireless network. When connecting to a Wi-Fi network, devices typically need to provide authentication credentials, such as a password or security key, to establish a secure connection.
- Wireless Access Points – Wi-Fi networks are set up using access points (APs) or routers, which act as central hubs for wireless connections. Access points receive and transmit Wi-Fi signals, enabling multiple devices to connect and communicate within the network.
- Wi-Fi Modes – Wi-Fi devices can operate in different modes, including infrastructure mode and ad-hoc mode. In infrastructure mode, devices connect to an access point or router for network access. In ad-hoc mode, devices can connect directly to each other without the need for an access point, forming a peer-to-peer network.
- Data Transfer Rates – Wi-Fi supports varying data transfer rates, depending on the Wi-Fi standard and the capabilities of the devices and network infrastructure. Newer Wi-Fi standards offer higher data rates and improved performance, allowing for faster wireless communication.
- Range and Coverage – The range and coverage of Wi-Fi networks depend on factors such as the power of the access point, the frequency band used, obstacles in the environment, and interference from other devices. Access points set to a 2.4Ghz frequency that are correctly placed should offer you coverage for 150 feet indoors and about 300 feet outdoors.
WIFI Security Protocols
- Wired Equivalent Privacy (WEP) – This was the original form of encryption used by wirless networks, however due to a security attack technique known as ‘packet sniffing’, the encryption technology was very easy to break.WPA / WPA2 – The weaknesses in WEP led to the development of the more secure WPA/ WPA2 encryption technologies. These are far more secure specifications, however they can still be hacked eventually.
TCP/IP
TCP / IP Protocol
The TCP/IP (Transmission Control Protocol/Internet Protocol) protocol suite is a set of communication protocols that are used to establish connections and enable data exchange between devices on the internet and other interconnected networks. It is the fundamental protocol suite of the internet and serves as the basis for most network communications.
TCP/IP consists of two main protocols: TCP and IP. Let’s explore each of them:
- Internet Protocol (IP):
- IP provides the basic addressing and routing functions in the TCP/IP suite. It assigns unique IP addresses to devices on the network, allowing them to be identified and located.
- IP is responsible for breaking data into small packets and forwarding them across the network to their destination based on the destination IP address.
- The current widely used version of IP is IPv4 (Internet Protocol version 4), which uses 32-bit addresses. However, due to the increasing demand for IP addresses, IPv6 (Internet Protocol version 6) was introduced, which uses 128-bit addresses and offers a significantly larger address space.
- Transmission Control Protocol (TCP):
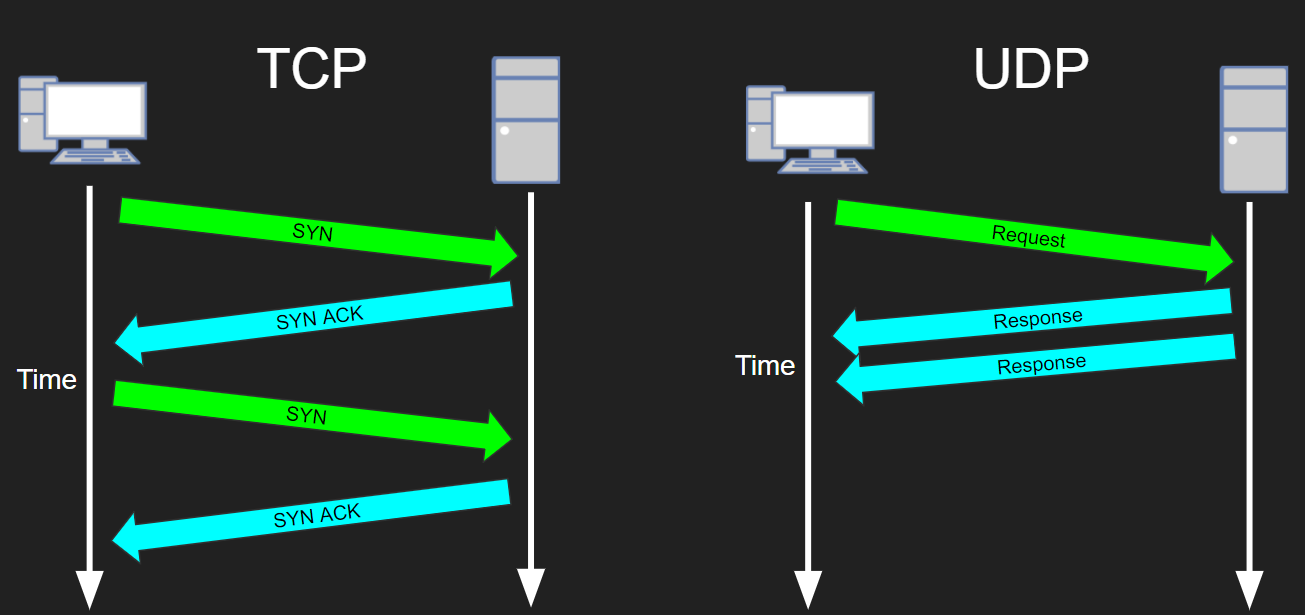
- TCP provides reliable, connection-oriented data delivery over IP.
- It establishes a virtual connection between two devices, ensuring the reliable and ordered delivery of data.
- TCP breaks data into segments and adds sequence numbers to each segment for reassembly at the destination. It also performs error detection and flow control to manage the reliable transmission of data.
- TCP guarantees that all segments are received, reordering them if necessary and requesting retransmission of lost segments.
- Website connections, FTP and Email rely on TCP.
- User Datagram Protocol (UDP):
- Similar to TCP, UDP is a transport protocol, but it is connectionless and provides unreliable, low-overhead data transmission. It is often used for time-sensitive applications or situations where data loss is acceptable.
- Example Uses – Voice over IP (VoIP), online games, and media streaming.
- Similar to TCP, UDP is a transport protocol, but it is connectionless and provides unreliable, low-overhead data transmission. It is often used for time-sensitive applications or situations where data loss is acceptable.
HTTP(S)
Hyper Text Transfer Protocol (Secure)
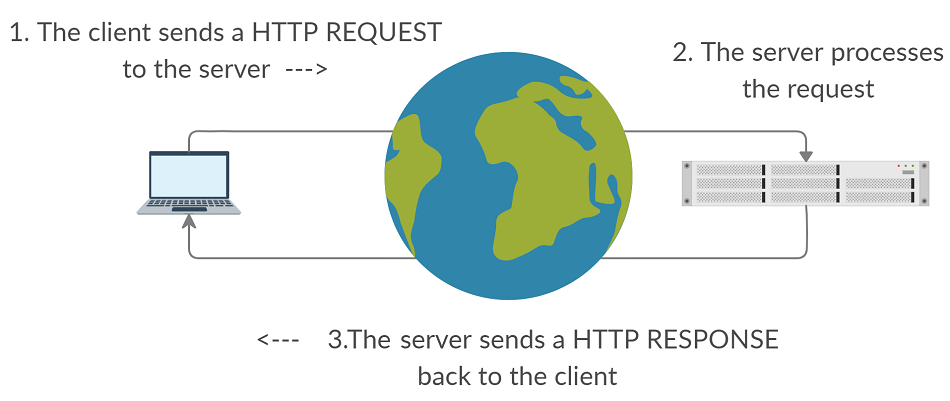
HTTP is the foundation for how website data (HTML Files, Images) is sent and received on the internet.
HTML is a stateless and connectionless protocol that operates at the Application Layer of the IP protocol stack. A request is made by a client computer (usually by a web browser) and the server then sends a response to the client.
Types of HTTP Requests
Common types of HTTP requests include:
- GET – This is a request for data from a web server(such as a HTML page or a CSS file)
- POST – This is where data is sent to a web server (such as the contents of a form that the user has filled in)
- PUT – This requests that a file on a server be updated
- DELETE – The requests that a file on a server be deleted.
- More request types can be found here.
Response Codes
When a page or file is requested the server usually sends a response code with the response.
Common HTTP Response Codes Include:
- 200 – OK
- 300 Moved Permanently. The URL of the requested page has been moved permanently
- 401 Unauthorized. The client has not been authenticated with the system.
- 403 Forbidden. The client is authenticated but does not have the access privileges to perform the action.
- 404 Not Found. The requested resource cannot be found at the location specified.
- 500 Server Error. The server have encountered an internal error somewhere.
FTP(S)
File Transfer Protocol (Secure)
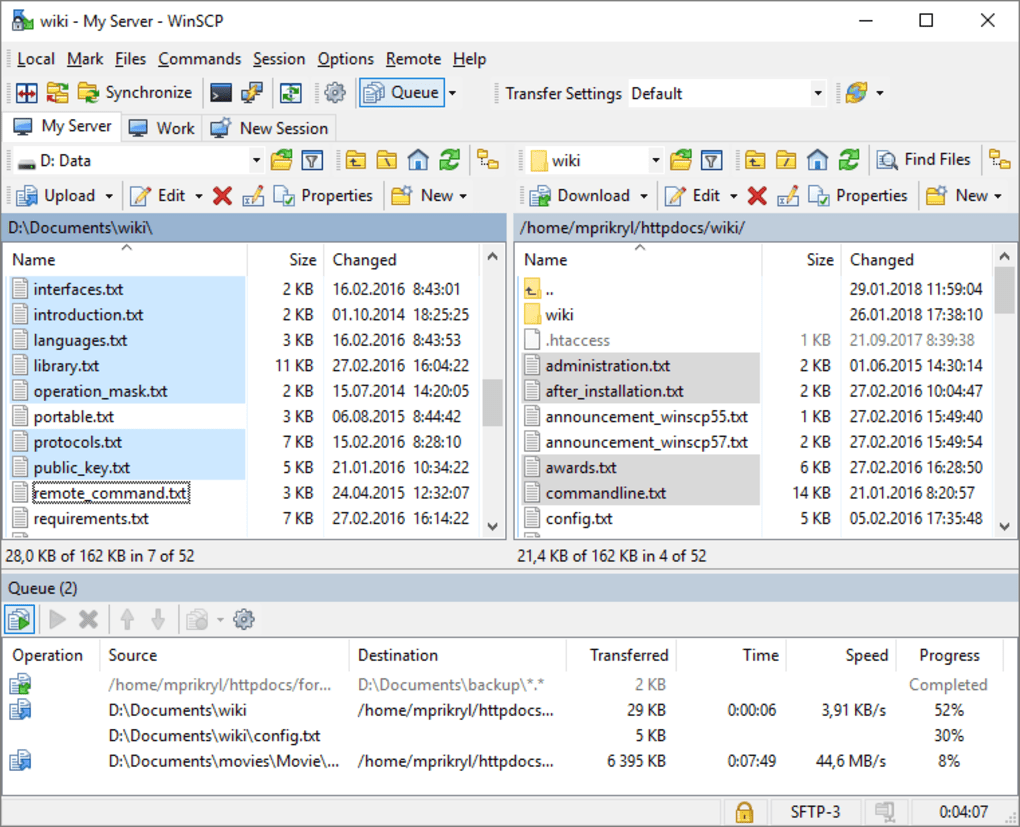
Original protocol used to transmit and receive files over the internet. FTP is a stateful connection, meaning a connection between client and server is established and maintained for the duration of use.
Can be used by:
- Web Browsers to download files
- FTP Programs to upload to/download from servers on the internet. Example software includes WinSCP, FileZilla.
SMTP
Simple Mail Transfer Protocol
SMTP is used for sending out email from an email client (such as Outlook / Apple Mail) to an email server. It is also used for relaying email messages from one server to another, which is necessary if the sender and recipient use different email server providers.
POP3
Post Office Protocol
POP3 is used to retrieve email messages from a server for display within an email client on the client pc. POP3 is different from POP because it contains additional authentication systems that stop unauthorized/malicious email access.
The POP procedure is as follows:
- Connect to the email server and authenticate
- Retrieve outstanding emails from the server
- Delete retrieved emails from the server (optional)
- Disconnect from the server
IMAP
Internet Message Access Protocol
This protocol is similar to POP3 except that it offers more functionality, such as:
- Mail Synchronization
- Multiple Folder based organization on the web server.
IMAP is the most common protocol to be used by large organizations for mail retrieval.
BitTorrent
BitTorrent
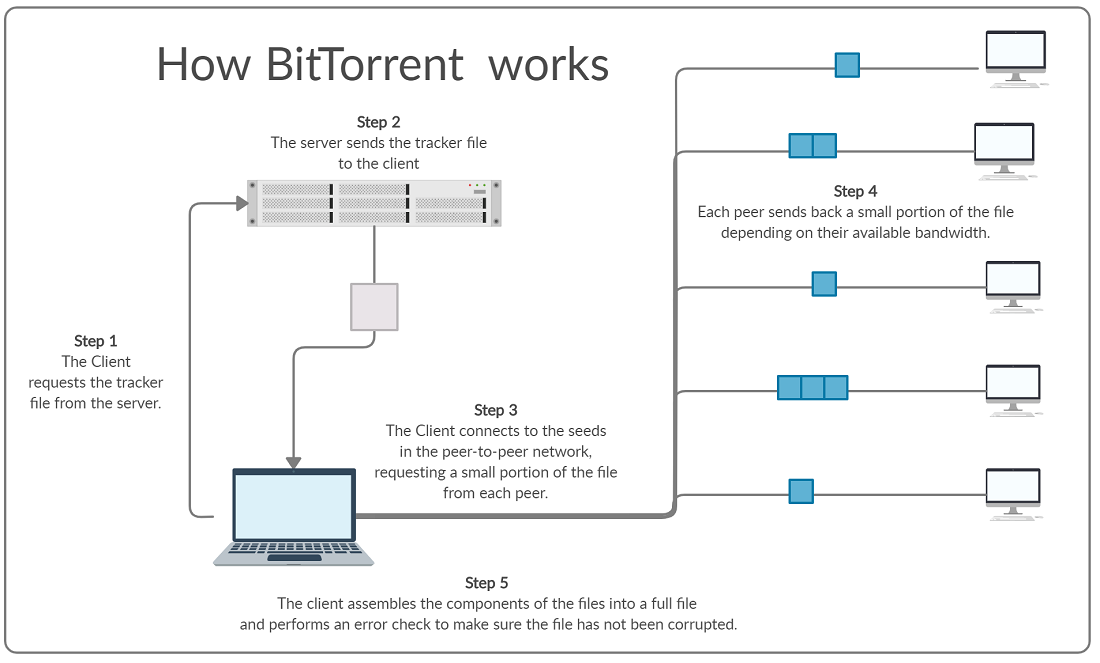
BitTorrent is a Peer-to-Peer file sharing protocol used for high speed transfer of large files across the internet. It differs from downloading from a normal server in that you don’t download the file from a single file server, but from multiple peers.
How it works
A Central Server contains the tracker file. This file does not contain the file you wish to download, but it contains the IP addresses of current seeds for the file, as well as other information about the file that is used to reassemble the file and check for errors.
A seed is a peer on the network who is hosting the file for download and hosting a file for download is known as seeding. When you download a file via BitTorrent the Client software your computer connects to multiple different seeds and downloads a small portion from each. Because you are downloading from multiple sources at once your client is able to achieve higher download speeds than if multiple clients were all connected to one server. Downloading a file is known as leeching. The total collection of seeding & leeching clients on the network are known as the swarm.
Once the complete file has been downloaded it needs to be checked to ensure that it has been fully downloaded correctly. This is achieve through the use of a checksum.
Resources
Resources