Starter
Intro
Encryption Algorithms
What is encryption?
Encryption is the scrambling of data so that only the intended recipient of data can decode and read it. In the starter you successfully decrypted anagrams to read the hidden word. This is a form (albeit very weak!!!) of encryption!
What is it used for?
Encryption is used for a wide variety of purposes, including:
- Stopping unauthorised people accessing your school reocrds
- Protecting internet shopping transactions
- Securing online banking transactions
- Keeping your social media messages private
Caesar
Caesar Shift Cipher
The Caesar Shift is named after Julius Caesar, who used it to encrypt all messages of military significant. It is a form of substitution cipher, where letters were ‘shifted’ along the alphabet by a certain number of letters. Caesar used a shift of 3 in all his ciphers.
3 Shift example
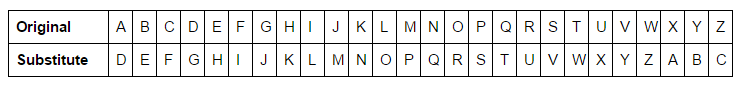
Using the 3 Shift example above you can encrypt a message…
Original: IHATESPROUTS
Coded: LKDWHVSURXWV
As you can see by the table above, letter G would be changed to J, M to P. To decrypt the message, you simply reverse the process.
Encryption Strength
- In Caesar’s lifetime there were no known records of his cipher being broken by the enemy, although this is likely because often the enemy would be illiterate.
- In practice this algorithm is very easy to break, either manually, or with the aid of a computer and is extremely insecure.
Vigenere
Vigenère Cipher
An improvement on the Caesar cipher was the Vigenère Cipher. It uses a series of shift ciphers, with each individual key being shifted by a certain amount, depending on a codeword (key).
In order to encrypt a message you would start with your message, and underneath each letter you would write the next letter in the key ( and just keep repeating if your code word is not very long).
You would then look up against the two axes of the Vigenère square(right) to find the coded letter.
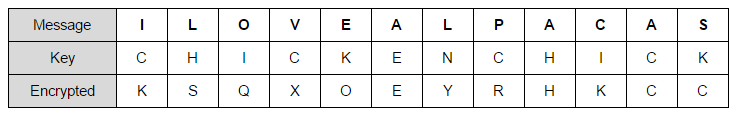
Example
Message: I like alpacas
Key: chicken
Coded message: KSQXOEYRHKCC
Encryption Strength
- The Vigenère Cipher is far stronger than the Caesar Shift – so strong in fact that it took 300 years to break it!
- It can be broken, however, as famously demonstrated by Charles Babbage – the inventor of the first computer!
- It would take a modern computer mere milliseconds to break this cipher and therefore it is not secure enough for modern communications.
Activity
Activity 1 – Secret Messages

Caesar Shift
Using the Caesar Shift Algorithm, write a secret message to a friend using a shift of your choice. See if you friend can break you cipher and find out the message!
Vigenere Cipher
If you have time, now try writing a vignere shift cipher using a message and code word of your choice. Pass in on to your friend to decrypt – but remember to give them the key(codeword) otherwise it might take them a long, long time to break the code!
Enigma
Enigma Machine

With the invention of the telephone and radio communications, military commanders now possessed the ability to control the forces from hundreds or thousands of miles away. The form of communication was easily and stealthily intercepted by the enemy, so the need for encryption was greater than ever. At the end of the first world war the German military developed the Enigma machine, a device designed to make encryption impossible to break.
The Enigma machine used a complex combination of rotors, wires and plugs on a typewriter style machine to encrypt and decrypt data.
A daily codebook of machine settings were needed in order to set the machine up in the correct of way each day. Without these settings it was impossible to manually break the codes.
Breaking the Enigma (Cribs and Brute Force)
At the start of the second world war Polish intelligence gave the British a working version of the Enigma machine, together with their research. A British team, headed by Alan Turing, then began working on a machine break the Enigma encryption. The Enigma machine had 107,458,687,327,300,000,000,000 possible combinations and at the time ( and until very recently) such a large number of combinations would have been impossible to attack.
The British were immensely aided breaking the enigma by the Germans themselves, who through poor operator discipline and human error helped the British team. For example many messages from the navy began with the words ‘Wettervorhersage’ (weather forecast), which massively helped the allies as they could perform probable-phrase attacks on the cipher. The British Bombe machine checked through each of these probably phrases to find a match.
Soon British intelligence were able to break the intercepted codes within about 2 days of them being received, which gave them a massive tactical and strategic advantage, especially because even until the end of the war the Germans believe the Enigma machine to be unbreakable.
Computer Based Attacks
If the German Enigma operators had maintained good working practices the Enigma ciphers would have likely remained unbreakable for the duration of the war, as a brute force attack (where every possible combination is attempted) would have taken the WW2 machines too long to work through. Even with all the processing power of modern super computers that governments have at their disposal it might take a day to break the codes.
Modern Encryption
Modern Encryption

Most modern systems use a form of Asymmetric Encryption using public and private keys.
The process
- The receiver’s public key is sent over the internet from the receiver to the sender and can only be used to encrypt data.
- The sender encrypts the data using the public key and sends the data to the receiver.
- The receiver uses their private key to decrypt the data.
The strength of the Asymmetric Encryption depends on the the length of the key (longer the better). A 128 bit encryption key has over 339,000,000,000,000,000,000,000,000,000,000,000 combinations to test using a brute force attack. This would take years to break using modern computing power.
